- Little Snitch Ignore Code Signature Free
- Little Snitch Reviews
- Little Snitch Mac
- Little Snitch Ignore Code Signature Meaning
A security vulnerability was recently disclosed by Josh Pitts, a security researcher at Okta. Free graillon 2 vst download. This vulnerability affects third-party macOS apps that check the code signatures of other apps by tricking them into treating a maliciously crafted fat binary as coming from Apple. You can read all the details about this in Josh’s blog post.
Because this also affects Little Snitch, Josh contacted us back in April with all the information we needed and enough time to fix this before he disclosed the issue this week. We also disclosed this as CVE-2018-10470.
Little Snitch started to verify the code signatures of apps and processes that use network connections in version 4, released almost a year ago in July 2017. Little Snitch versions 4.0 to 4.0.6 are affected by this vulnerability and Little Snitch 4.1 released yesterday fixes this issue.
Fortunately for us and our users, the consequences this has for Little Snitch are not as as bad as it first seems when reading the variousheadlinesaboutthisissue: What connections are allowed or denied by Little Snitch’s network filter is completely unaffected by this. The only thing that could happen is that Little Snitch would show inconsistent or incorrect information about an app’s code signature, but it would never actually allow connections that should not be allowed.
A Little More Detail
Jan 14, 2020 Key Features of Little Snitch Torrent. The latest silent mode feature is an alternative, to confirm several and single connection alerts. Now the users can make and change rules within a click. Therefore cord signature safe filter secure operations without a proper code signature. Jan 20, 2020 Little Snitch 4.4.4 Crack is a fantastic tool that is available for Win and Mac. It works as a firewall. Little Snitch monitors activities of your system. Actually monitors what is ongoing inside your Mac. Little Snitch keeps in the eys the activities of the application running. Mar 15, 2020 Little Snitch 4.5.2 Crack is the fabulous software that comes with the authority to assist to keep your Mac protected by scrutinizing the connections.This is a powerful application that allows you to control the inbound plus outbound traffic. Little Snitch purifies and expands this friendly firewall. Mar 30, 2020 The focus is now on checking for modifications with the best means available. That is usually still the code signature but for programs that are not code signed, Little Snitch now computes a secure hash over the program’s executable. (There’s still a warning if a process is not signed, but only to inform you about a possible anomaly.). Jun 13, 2018 The bottom line is that Little Snitch does not allow connections if you have a rule that requires a valid code signature, but the running process’ code signature does not match that. It’s a bit different from the example above if you don’t have any rules for the app beforehand.
The issue discovered by Josh concerns fat binaries that contain code slices for multiple architectures (e.g. i386, x86_64, PowerPC) whereas the first architecture is signed correctly by Apple. When security tools would verify the code signature of such a fat binary, they would only check the first slice and assume that if that one is OK, the whole fat binary is OK. This means that they effectively ignore the code signature of all other slices, allowing attackers to put arbitrary code there.
What makes all this less of a problem for Little Snitch is that the actually relevant check happens in a kernel extension. Because the macOS kernel only knows about the code signatures of processes that are running, it only knows about the code signature of the correct slice. And since Little Snitch’s kernel extension uses this information to determine whether a running process has a valid code signature or not, it is completely unaffected by the issue discovered by Josh.
The parts of Little Snitch where this vulnerability manifests itself are Little Snitch Configuration, Network Monitor, and the connection alert. When these components try to verify the code signature of an app on disk, they will show incorrect information for the reasons outlined above. That’s bad, but still not as bad as you might think. Let’s play through what would happen here.
Little Snitch Ignore Code Signature Free
An Example
Let’s assume you have an universal app on your Mac that contains a maliciously crafted fat binary containing slices for two architectures. The first slice is signed by Apple and the second slice has no code signature. The second slice is being executed.
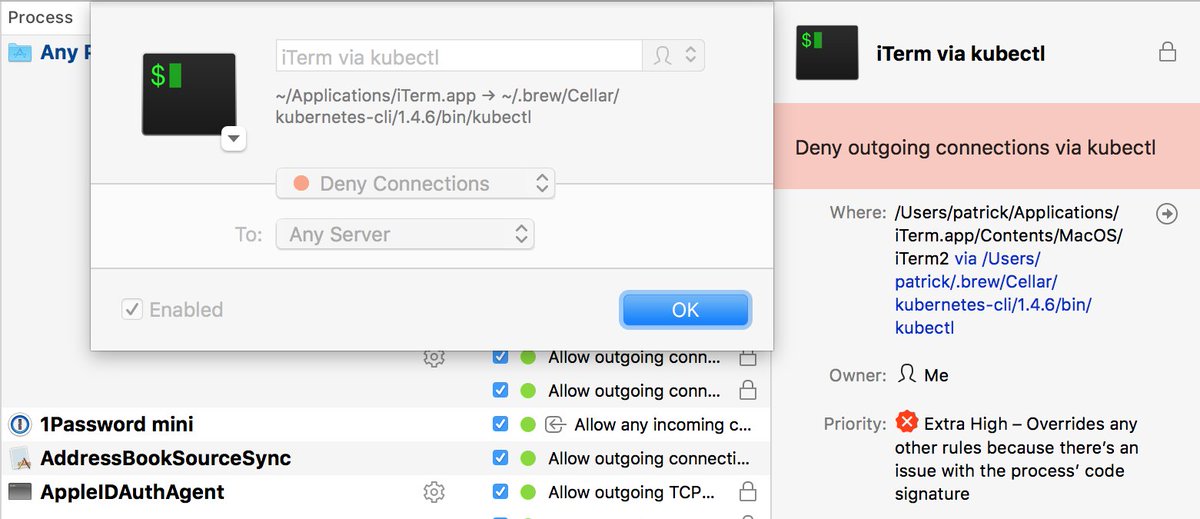
- You check the code signature of the app in Little Snitch Configuration and it incorrectly shows that the app is signed by Apple.
- You trust this incorrect information and create a rule that allows connections. This rule requires a valid code signature by Apple (unless you specifically opt-out of all code signature checks for that app).
- The app tries to connect.
- Little Snitch’s kernel extension sees that the rule requires a valid code signature by Apple. But the running process is based on the second slice of the fat binary and has no code signature. We call this a code signature mismatch.
- Little Snitch shows a connection alert that prominently notifies you about this mismatch. The default option in this alert is to deny any connection by the app.
The bottom line is that Little Snitch does not allow connections if you have a rule that requires a valid code signature, but the running process’ code signature does not match that.
It’s a bit different from the example above if you don’t have any rules for the app beforehand. Little Snitch will still show a connection alert for the maliciously crafted app and inform you with a big, yellow warning icon that the code signature of the running process is not valid.
In Conclusion
This issue shows once more that code signatures involve more complexity than just a cryptographic signature on a file. The code goes through many stages before it is actually executed by a CPU and the integrity of the signature must be preserved throughout all these stages. Little Snitch’s help chapter on code signature issues is a testimony to this.

Little Snitch Crack Torrent Full Latest Version Download
Little Snitch Crack Patch is a very powerful latest Securityprovider application for MAC OS. It works in the background and provides safeguardduring surfing the internet. This app avoids all the viruses, malware, adwareand spy wares that may come to the computer unknowingly. It works in twodifferent modes and operates in Alert mode where you can perform immediateactions against any violation. Secondly, it can also work in a Silent modewhere you can perform actions against malicious activity later. LittleSnitch License Key is the best-ever opportunity to monitor malevolentactivities even if you know or not.
Little Snitch Reviews
Little Snitch Crack Serial Key Updated keygen
Little Snitch Mac
You can view your network traffic flow from the MAC network. It tells you about the network rules why it blocks the site and what is the problem. Also, it can measure and display Real-time network traffic flow by using diagrams, charts, and other statistics. Little Snitch 4 Crack registration key can capture the snapshot of your network flow easily. It will make a simple well-organized list of domains connected with your MAC. Also, it analyses the data volume and measures the bandwidth of every domain. You can also search for a specific position of any domain by the Little Snitch Crack Quick filters option.
We still have titles for 23 systems and this will not change in the foreseeable future!Featured Games. Removed Due to CopyrightsThis page has been removed due to a request from Nintendo of America Inc.We are very grateful to have served the emulation community for so many years and to have CoolROM still exist today. /cooking-mama-download-rom.html. We feel we have reached this goal and helped cure more cases of nostalgia than we could have ever imagined.Thank you for all of your support throughout the years - CoolROM will continue strong. From the very beginning, our goal was to allow users to re-live classic moments from video games that they have lost and cannot purchase anymore.
Little Snitch 4.4.3 Crack License key Generator For Mac
This is an application that screens and deal with all approaching an active association in Mac OS X and furthermore in your Windows. And in addition, Little Snitch Keygen is a firewall to keep your Mac from surprising visitors from the tremendous web sources. In addition, the web is the most significant and colossal place of association. You know some associations are not confided in then Little Snitch is the best application to screening all associations. In another way, it shields your Data from sending or sharing out through the web. Besides, this application anchors your protection and involves the active information on your Mac.
Little Snitch Ignore Code Signature Meaning
You may also love to download MacBooster Crack with License Key is the best software for system maintenance.
Key Features
- Little Snitch Torrent Crack 2020 also can figure out the reason for allowed or denied connections.
- This is a modern and fast monitoring research assistant.
- Examine the code signature with huge information.
- It also permits you to reserve a decision just in few moments.
- Keep the record in the snapshot of the present status and full connection by later analysis.
- Display the aggregate activity sums, transmission ability, and top movement.
- Flexible arranging and combining the options.
- Latest corresponding principles about connections.
- Provide you a sign of association denied by it.
- Little Snitch 4.4.3 Crack also gives you a full effective spare snapshot for the investigation.
- Complete capture organizes a movement in PCAP sequence.
What’s New?
- Added support for a new remote endpoint type in the internet policy.
- Fix a problem where clicking on a column header did not properly sort the list
- Now, users have the possibility to restore a backup from protected and privacy folders such as Desktop and Documents.
- Decrease the length of Snap in PCAP files
- It will never load CPU now when Network Monitor is inactive
- Update rule sorting in configuration
- Fix other a lot of bugs and improved performance
- The latest version has many improvements and updates some old features
- Added compatibility for WireGuard VPN
- Also, fix the problem related to Network Monitor that traffic captures were incomplete
System Requirements
Before you start Little Snitch Crack Serial Number download,make sure your PC meets minimum system requirements.
- Operating System: Mac OS X 10.11 or Higher.
- CPU: Intel Dual-Core or later.
- Memory (RAM): 1GB of RAM required.
- Hard Disk Space: 300 MB of free space required.
- Display: 1280 × 768 screen resolution, 32-bitcolor.
How to use Little Snitch 4.4.3 Crack?
- Firstly, download and install the Little Snitch Crack file from the given link below.
- Unpack crack files and Install the Crack
- Copy all cracked files from crack folder to install directory
- Your product is fully activated now
- Finally, Enjoy the Little Snitch Pro full version.